-

Addressing Security Challenges in Linux's io_uring Interface
Explore security challenges in Linux's io_uring interface and strategies to mitigate stealthy rootkit attacks.
-

Espionage Threats: Android.Spy.1292.origin and Military Cybersecurity
Explore the espionage threat of Android.Spy.1292.origin targeting military cybersecurity via a mapping app.
-

WhatsApp's Advanced Chat Privacy: A New Era of Secure Messaging
Explore WhatsApp's new Advanced Chat Privacy feature enhancing secure messaging with robust privacy controls and AI restrictions.
-

Blue Shield of California Data Breach: A Wake-Up Call for Healthcare Security
Blue Shield's data breach exposes healthcare security flaws, impacting trust and prompting legal and regulatory scrutiny.
-

The Escalating Threat of Cybercrime: A $16.6 Billion Wake-Up Call
Explore the $16.6 billion impact of cybercrime in 2024 and its implications for businesses and individuals.
-
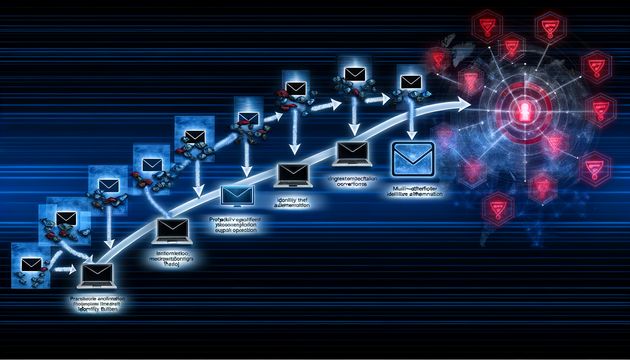
The Evolution of Phishing Attacks: From Links to Identity Theft
Explore the evolution of phishing attacks from simple scams to complex identity theft operations challenging security measures.
-

Understanding and Mitigating CVE-2024-54085: A Critical BMC Vulnerability
Explore CVE-2024-54085, a critical BMC vulnerability, its impact, and mitigation strategies for server security.
-

Marks & Spencer Cyberattack: A Wake-Up Call for Retail Cybersecurity
Marks & Spencer cyberattack highlights retail vulnerabilities and the need for robust cybersecurity measures.
-

Understanding the Impact of the Active! Mail Vulnerability
Explore the critical Active! Mail vulnerability impacting over 11 million accounts, highlighting the need for robust cybersecurity measures.
-

The 'Elusive Comet' Cyber Threat: A Deep Dive into Cryptocurrency Attacks
Explore the 'Elusive Comet' cyber threat targeting cryptocurrency via Zoom exploits and social engineering tactics.
-

Understanding the SK Telecom Malware Attack: Lessons for the Telecom Industry
Explore the SK Telecom malware attack and its implications for telecom security and USIM data protection.
-

Ripple's xrpl.js Library Breach: A Wake-Up Call for Cryptocurrency Security
Ripple's xrpl.js library breach exposes cryptocurrency security risks, highlighting the dangers of supply chain attacks.
-

Understanding and Mitigating the Cookie-Bite Attack
Explore the Cookie-Bite attack, a threat exploiting browser extensions to steal Azure Entra ID session cookies, bypassing MFA.
-

Microsoft Entra ID Glitch: Lessons from a Security Feature Misstep
Explore the Microsoft Entra ID glitch and its impact on security, highlighting lessons learned from a misstep in feature deployment.
-
The Rise of ClickFix: A New Social Engineering Threat
Explore ClickFix, a new social engineering threat used by state-sponsored hackers to bypass security measures and spread malware.
-

Exploiting Google OAuth: The DKIM Replay Attack Threat
Explore how phishers exploit Google OAuth in DKIM replay attacks, posing significant email security threats.
-

Unmasking Scallywag: A Deep Dive into a Massive Ad-Fraud Operation
Explore the Scallywag ad-fraud operation, generating 1.4 billion fake ad requests daily, and its impact on digital advertising.
-

Navigating Microsoft Entra's New Security Features: Balancing Protection and Usability
Explore Microsoft Entra's new security features, balancing protection with usability, including Smart Lockout and MFA integration.
-

Understanding and Mitigating CVE-2025-32433: A Critical Erlang/OTP Vulnerability
Explore CVE-2025-32433, a critical Erlang/OTP vulnerability, and learn mitigation strategies to protect your systems.
-

SuperCard X: A New Era of Mobile Malware
Explore SuperCard X, a sophisticated mobile malware using NFC relay attacks and minimal permissions to evade detection.
-

The Rise of ClickFix Attacks: Understanding the Interlock Ransomware Gang
Explore the rise of ClickFix attacks by the Interlock ransomware gang and their impact on cybersecurity.
-

Understanding the Threat: Scammers Posing as FBI IC3 Employees
Scammers impersonate FBI IC3 employees, using tech and psychology to deceive victims and exploit financial vulnerabilities.
-

Understanding the Critical Authentication Bypass Flaw in ASUS Routers
Explore the critical authentication bypass flaw in ASUS routers, its risks, and mitigation strategies to secure your network.
-

Understanding and Mitigating the SonicWall SMA Vulnerability
Explore the evolving SonicWall SMA vulnerability and learn essential mitigation strategies to protect against active cyber threats.
-

The MysterySnail RAT: An Evolving Cyber Threat
Explore the evolving threat of MysterySnail RAT, targeting Russian entities with advanced espionage capabilities.

