The Rise of ClickFix: A New Social Engineering Threat
In recent times, state-sponsored hackers have adopted a clever social engineering tactic known as ClickFix. This method, popular among cybercriminal groups from North Korea, Iran, and Russia, takes advantage of everyday user interactions with digital interfaces to spread malware. First spotted in early 2024, ClickFix was initially used by groups like TA571 and the ClearFake cluster. It has since become a key tool for state-sponsored actors (BleepingComputer).
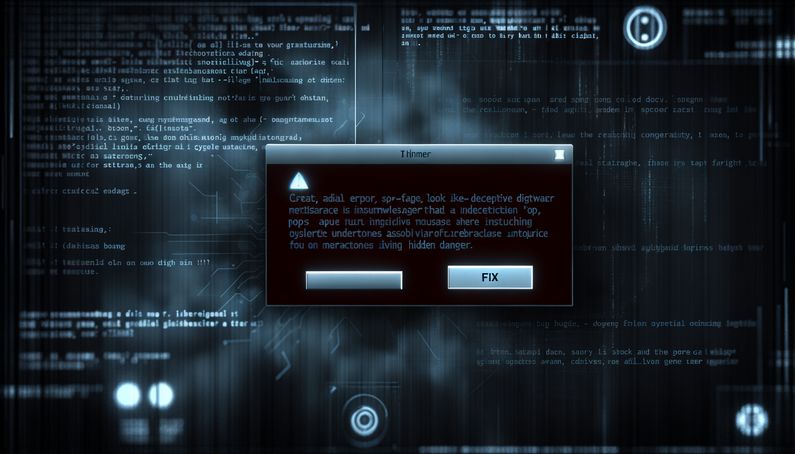
The tactic works by creating fake error messages that look like real software notifications, tricking users into clicking a ‘Fix’ button. This simple action can trigger malicious scripts, bypassing traditional security measures like Endpoint Detection and Response (EDR) systems, which are tools designed to detect and respond to threats on a network (Security Boulevard). As a result, ClickFix has become a powerful tool in cyber-espionage campaigns, especially for groups like North Korea’s Kimsuky, which has targeted think tanks with fake emails (Proofpoint).
Understanding ClickFix
Evolution of ClickFix
ClickFix has emerged as a prominent social engineering tactic, mainly used by state-sponsored hackers from North Korea, Iran, and Russia. Its popularity stems from its simplicity and effectiveness in bypassing traditional security measures. Initially observed in early 2024, ClickFix was first deployed by cybercriminal groups such as TA571 and the ClearFake cluster. Over time, it has been adopted by state-sponsored actors, becoming a significant threat in cyber-espionage campaigns (BleepingComputer).
How ClickFix Works
ClickFix exploits routine user interactions with digital interfaces. It involves creating fake error messages that mimic legitimate software or document-sharing platforms. These messages typically inform users of a failed document or download, prompting them to click a ‘Fix’ button. This action leads to the execution of a PowerShell or command-line script, which installs malware on the victim’s device. Imagine receiving a pop-up that looks like a typical software update alert, but instead of fixing an issue, it installs harmful software. This method easily bypasses security solutions like Endpoint Detection and Response (EDR) and Secure Web Gateways (SWG), which are systems that filter and monitor web traffic to prevent threats (Security Boulevard).
Adoption by State-Sponsored Actors
State-sponsored groups have increasingly adopted ClickFix due to its effectiveness in espionage operations. Notably, North Korea’s Kimsuky group used ClickFix in a campaign targeting think tanks focused on North Korea-related policy. The attackers employed spoofed emails, appearing as Japanese diplomats, to initiate contact with targets (Proofpoint). Similarly, Iranian group MuddyWater and Russian groups APT28 and UNK_RemoteRogue have integrated ClickFix into their attack chains, leveraging its ability to deceive users into executing malicious commands (TechRadar).
Impact on Security Measures
The rise of ClickFix has significant implications for cybersecurity practices. Traditional security measures, such as antivirus software and firewalls, are often insufficient to detect and block ClickFix attacks. This is because the tactic relies on social engineering rather than exploiting technical vulnerabilities. As a result, organizations must enhance their security awareness training to educate users about the dangers of unsolicited command execution and the importance of verifying the authenticity of error messages (Field Effect).
Countermeasures and Mitigation Strategies
To mitigate the threat posed by ClickFix, organizations should implement a multi-layered security approach. This includes deploying advanced threat detection systems capable of identifying and blocking suspicious activities, such as unauthorized script execution. Additionally, regular security awareness training should be conducted to educate employees about the risks associated with social engineering tactics like ClickFix. Users should be encouraged to verify the legitimacy of error messages and avoid executing commands they do not understand (Cyber Security News).
Future Trends and Developments
As ClickFix continues to evolve, it is likely that attackers will develop more sophisticated variations of the tactic to evade detection. This may involve integrating ClickFix with other attack vectors, such as ransomware or supply chain attacks, to increase its impact. Organizations must remain vigilant and adapt their security strategies to address these emerging threats. Continuous monitoring and analysis of threat intelligence will be crucial in staying ahead of adversaries and protecting sensitive information from being compromised (GBHackers).
Final Thoughts
The rise of ClickFix underscores the evolving landscape of cybersecurity threats, where social engineering tactics are increasingly favored over traditional hacking methods. As organizations grapple with this new reality, enhancing security awareness and implementing advanced threat detection systems become paramount. The simplicity and effectiveness of ClickFix highlight the need for continuous adaptation in cybersecurity strategies to protect against such deceptive tactics (Field Effect).
Looking ahead, the potential integration of ClickFix with other attack vectors, such as ransomware, poses a significant challenge. Organizations must remain vigilant, leveraging threat intelligence and adopting a multi-layered security approach to stay ahead of adversaries. As attackers refine their methods, the cybersecurity community must also evolve, ensuring robust defenses against these sophisticated threats (GBHackers).
References
- BleepingComputer. (2024). State-sponsored hackers embrace ClickFix social engineering tactic. https://www.bleepingcomputer.com/news/security/state-sponsored-hackers-embrace-clickfix-social-engineering-tactic/
- Security Boulevard. (2025). ClickFix: Social engineering that bypasses EDRs, SWGs, and humans. https://securityboulevard.com/2025/03/clickfix-social-engineering-that-bypasses-edrs-swgs-and-humans/
- Proofpoint. (2025). Around the world in 90 days: State-sponsored actors try ClickFix. https://www.proofpoint.com/us/blog/threat-insight/around-world-90-days-state-sponsored-actors-try-clickfix
- Field Effect. (2025). ClickFix: Rising threat of fake fixes. https://fieldeffect.com/blog/clickfix-rising-threat-fake-fixes
- GBHackers. (2025). State-sponsored hackers now widely using ClickFix attack. https://gbhackers.com/state-sponsored-hackers-now-widely-using-clickfix-attack/



